In this Python & Boto3 lesson we want to learn How to Create AWS Custom Policy with Python & Boto3, so first of all let’s talk that what is custom policy in AWS.
What is Custom Policy in AWS?
AWS IAM policies define permissions for IAM entities (users, groups, roles) to access AWS resources. Custom policies are policies created by users to meet specific access control requirements that are not addressed by AWS-managed policies. Using Python and Boto3, you can dynamically create and manage custom IAM policies to enforce granular access control across your AWS environment.
Prerequisites:
Before we start crafting custom IAM policies with Python and Boto3, ensure you have the following prerequisites:
- Python installed on your system.
- Boto3 library installed (pip install boto3
). - AWS credentials configured on your system (either through AWS CLI or environment variables).
Also make sure that you have already read these three articles, because they are related to this article.
- How to install Boto3 and AWS CLI for Python
- How to Configure AWS CLI to Use Boto3
- How to Create AWS IAM User with Python & Boto3
Creating Custom IAM Policies with Python & Boto3
Let’s learn the steps involved in creating custom IAM policies programmatically using Python and Boto3:
Step 1: Import Boto3
Start by importing Boto3 library in your Python script:
|
1 |
import boto3 |
Step 2: Initialize Boto3 IAM Client
After that initialize the Boto3 IAM client to interact with AWS IAM:
|
1 |
iam = boto3.client('iam') |
Step 3: Define Policy Document
Create the policy document, and specify the permissions and resources to be granted access. The policy document is written in JSON format. use create_policy method to create the custom IAM policy, provide the policy name and policy document:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
policy_name = 'CodeloopPolicy' policy_document = { "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "s3:*", "Resource": "*" } ] } response = iam.create_policy( PolicyName=policy_name, PolicyDocument=json.dumps(policy_document) ) policy_arn = response['Policy']['Arn'] |
This is the complete code
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
import boto3 import json # Initialize Boto3 IAM client iam = boto3.client('iam') # Define policy name and policy document policy_name = 'CodeloopPolicy' policy_document = { "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "s3:*", "Resource": "*" } ] } # Create custom IAM policy response = iam.create_policy( PolicyName=policy_name, PolicyDocument=json.dumps(policy_document) ) # Extract the ARN of the created policy policy_arn = response['Policy']['Arn'] # Print the ARN of the created policy print("Custom IAM policy created successfully with ARN:", policy_arn) |
This code will create custom IAM policy named ‘CodeloopPolicy’, this policy has a permission of allowing all actions (s3:*) on all S3 resources (‘*’). Replace the policy_name and policy_document variables with your desired policy name and policy document.
Make sure you have installed Boto3 (pip install boto3) and configured your AWS credentials on your system before running this script. Also ensure that the IAM user executing this script has the necessary permissions to create IAM policies.
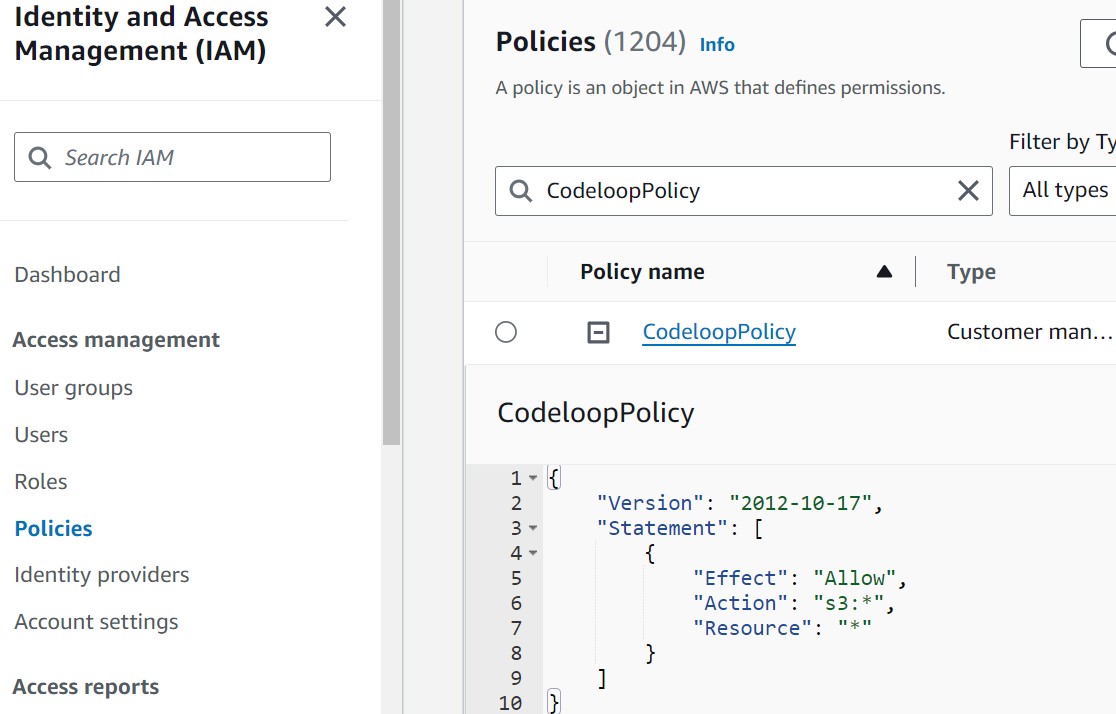
Run the code and custom policy will be created, now if you check AWS Management Console policy section, you will see that, go to IAM and then Policies, search the name of the policy in the search bar.
FAQs:
Q: What is the difference between AWS managed policies and custom policies?
A: AWS managed policies are pre-configured policies provided by AWS, and it is used for some cases. Custom policies, on the other hand are user-defined policies, to specific access control requirements not addressed by managed policies.
A: Can I attach custom policies to IAM users, groups, or roles?
Q: Yes, once you have created custom policies, then you can can attached that to IAM users, groups, or roles using Python and Boto3 to grant them the specified permissions.
Q: Are there any limitations to custom IAM policies?
A: Custom IAM policies are subject to certain limitations, such as size restrictions on policy documents and constraints on the number of policies that can be attached to IAM entities.
Q: Can I update or delete custom IAM policies programmatically?
A: Yes, you can update or delete custom IAM policies using Python and Boto3 by calling the appropriate methods (update_policy, delete_policy).
Learn More on AWS IAM:
Subscribe and Get Free Video Courses & Articles in your Email