In this AWS lesson we want to learn how to Attach AWS IAM Policy to IAM User with Python, as we already talked IAM policies define permissions for IAM entities (users, groups, roles) to access AWS resources. Some times in AWS it’s important to assign the appropriate policies to IAM users to ensure they have the necessary permissions for their roles.
AWS IAM Policy Attachments with Python & Boto3
IAM policy attachments associate IAM policies with IAM users, and it will grant them permissions defined in those policies. By attaching policies to users, you can control their access to AWS resources based on their roles and responsibilities. and attaching IAM Policy to AWS user with Python and boto3 simplifies the process and educes manual effort.
Prerequisites:
Before we delve into attaching IAM policies to IAM users with Python and Boto3, ensure you have the following prerequisites:
- Python installed on your system.
- Boto3 library installed (pip install boto3).
- AWS credentials configured on your system (either through AWS CLI or environment variables).
- An existing IAM user and IAM policy to attach.
Also make sure that you have already read these three articles, because they are related to this article.
- How to install Boto3 and AWS CLI for Python
- How to Configure AWS CLI to Use Boto3
- How to Create AWS IAM User with Python & Boto3
Also for creating users with Python and Boto3 and also creating custom policy, check these articles.
Attaching IAM Policies to IAM Users with Python & Boto3:
Let’s walk through the steps involved in attaching IAM policies to IAM users programmatically using Python and Boto3:
Step 1: Import Boto3
Start by importing the Boto3 library in your Python script:
|
1 |
import boto3 |
Step 2: Initialize Boto3 IAM Client:
After that initialize the Boto3 IAM client to interact with AWS IAM:
|
1 |
iam = boto3.client('iam') |
|
1 2 |
user_arn = 'arn:aws:iam::123456789012:user/username' policy_arn = 'arn:aws:iam::123456789012:policy/MyPolicy' |
Step 4: Attach IAM Policy to IAM User
Use the attach_user_policy method to attach the IAM policy to the IAM user:
|
1 2 3 4 5 6 |
response = iam.attach_user_policy( UserName='username', PolicyArn='arn:aws:iam::123456789012:policy/MyPolicy' ) print("IAM policy attached successfully:", response) |
Now this is the complete example in here we want to attach CodeloopPolicy to our codeloop-updated user that we already have created, you can check the above article for that, make sure to change that according to your username and policy.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
import boto3 # Initialize Boto3 IAM client iam = boto3.client('iam') # Specify IAM user and policy ARNs user_name = 'codeloop-updated' policy_arn = 'arn:aws:iam::121456538223:policy/CodeloopPolicy' # Attach IAM policy to IAM user response = iam.attach_user_policy( UserName=user_name, PolicyArn=policy_arn ) # Print response if needed print("IAM policy attached successfully:", response) |
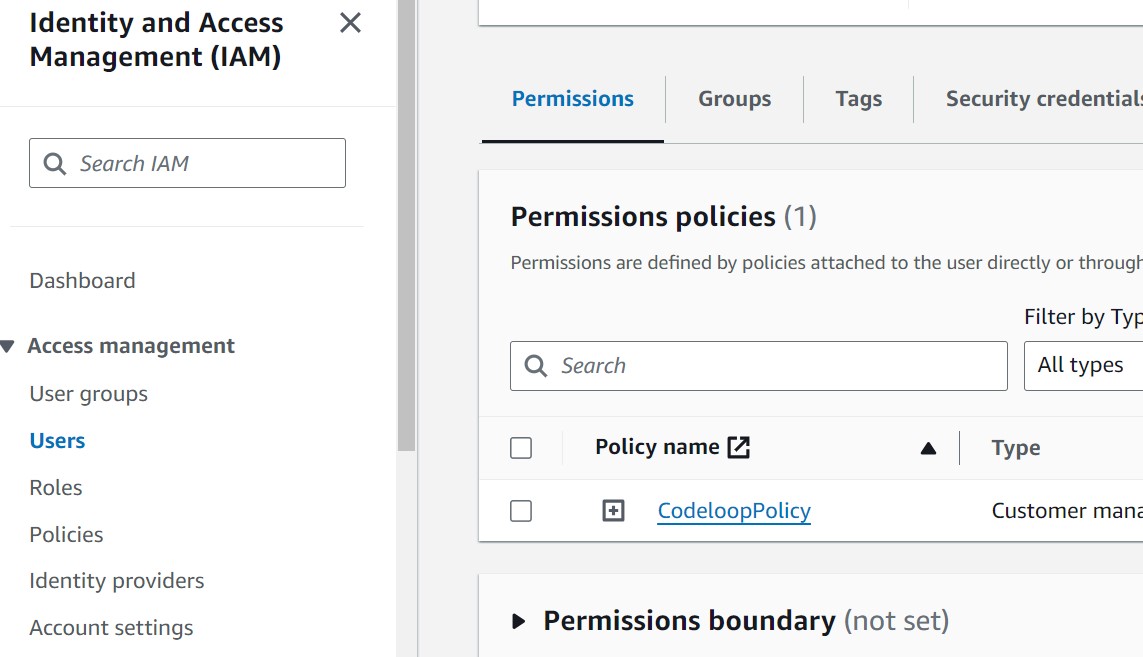
And now if you click on the specific user and go to the Permissions, you will see that the policy is attached to user.
FAQs:
What is an IAM policy attachment?
An IAM policy attachment associates an IAM policy with an IAM user, group or role, and it is granting the permissions defined in that policy to specific entity.
Why do we attach IAM policies to IAM users?
IAM policies are attached to IAM users to grant them specific permissions for accessing AWS resources. This allows organizations to control and manage user access to AWS services based on their roles and responsibilities.
Can I attach multiple IAM policies to a single IAM user?
Yes, you can attach multiple IAM policies to a single IAM user, and it allows you to grant them a combination of permissions according to their needs.
Subscribe and Get Free Video Courses & Articles in your Email